Agenda
-
- Autonomous System and BGP
- what is Site-to-Site VPN
- Flow Diagram and Architecture
- Site-to-Site VPN features
- Site-to-Site VPN limitations
- Customer gateway and Virtual Gateway
- Limitation
- Alternate VPN
- Demo
What is Autonomous System:
The Internet is a network of networks, and autonomous systems are the big networks that make up the Internet. More specifically, an autonomous system (AS) is a large network or group of networks that has a unified routing policy. Every computer or device that connects to the Internet is connected to an AS.
What is an AS routing policy?
An AS routing policy is a list of the IP address space that the AS controls, plus a list of the other ASes to which it connects. This information is necessary for routing packets to the correct networks. ASes announce this information to the Internet using the Border Gateway Protocol (BGP)
What is BGP?( Border Gateway Protocol)
ASes announce their routing policy to other ASes and routers via the Border Gateway Protocol (BGP). BGP is the protocol for routing data packets between ASes. Without this routing information, operating the Internet on a large scale would quickly become impractical: data packets would get lost or take too long to reach their destinations.
Each AS uses BGP to announce which IP addresses they are responsible for and which other ASes they connect to. BGP routers take all this information from ASes around the world and put it into databases called routing tables to determine the fastest paths from AS to AS. When packets arrive, BGP routers refer to their routing tables to determine which AS the packet should go to next.
With so many ASes in the world, BGP routers are constantly updating their routing tables. As networks go offline, new networks come online, and ASes expand or contract their IP address space, all of this information has to be announced via BGP so that BGP routers can adjust their routing tables.
AWS Site-to-Site VPN?
Gateway Types
- Instances that you launch into an Amazon VPC can’t communicate with your own remote (On-premises) network. You can enable access to your remote network from your VPC by creating an AWS Site-to-Site VPN connection and configuring routing to pass traffic through the connection.
- AWS Site-to-Site VPN creates encrypted tunnels between your network and your Amazon VPCs or AWS Transit Gateways. On the AWS side of the VPN connection, a Virtual Private Gateway or Transit Gateway provides two VPN tunnels (endpoints which use a unique public IP address) which you can simultaneously use for high availability and automatic failover (redundancy).
- on-premises (remote) network includes a customer gateway device, which you must configure to enable the Site-to-Site VPN connection. You set up the routing so that any traffic from the VPC bound for our network is routed to the virtual private gateway.
concepts for Site-to-Site VPN:
VPN connection: A secure connection between your on-premises equipment and your vpcs.
Vpn tunnel: an encrypted link where data can pass from the customer network to or from aws.
Customer gateway (cgw): a resource that you create in aws that represents the customer gateway device in your on-premises network.
Customer gateway device: a physical device or software application on your side of the site-to-site vpn connection.
Virtual Private Gateway (VGW): It is the VPN concentrator on the AWS side of the VPN connection. You have to attach it to the VPC from which you want to create the Site-to-Site VPN connection. (dynamic Routing)
Transit Gateway (TGW): It is a transit hub that you can use to interconnect your VPC and on-premises networks. You can create a VPN connection as an attachment on a transit gateway.
- the Amazon side of the Site-to-Site VPN connection.
Site-to-Site VPN features
The following features are supported on AWS Site-to-Site VPN connections:
- Internet Key Exchange version 2 (IKEv2)
- NAT traversal
- 4-byte ASN in the range of 1 – 2147483647 for Virtual Private Gateway (VGW) configuration. See Customer gateway options for your Site-to-Site VPN connection for more information.
- 2-byte ASN for Customer Gateway (CGW) in the range of 1 – 65535. See Customer gateway options for your Site-to-Site VPN connection for more information.
- CloudWatch metrics
- Reusable IP addresses for your customer gateways
- Additional encryption options; including AES 256-bit encryption, SHA-2 hashing, and additional Diffie-Hellman groups
- Configurable tunnel options
- Custom private ASN for the Amazon side of a BGP session
- Private Certificate from a subordinate CA from AWS Private Certificate Authority
- Support for IPv6 traffic for VPN connections on a transit gateway
Site-to-Site VPN limitations
A Site-to-Site VPN connection has the following limitations.
- IPv6 traffic is not supported for VPN connections on a virtual private gateway.
- An AWS VPN connection does not support Path MTU Discovery.
In addition, take the following into consideration when you use Site-to-Site VPN.
- When connecting your VPCs to a common on-premises network, we recommend that you use non-overlapping CIDR blocks for your networks.
Pricing
You are charged for each VPN connection hour that your VPN connection is provisioned and available. For more information, see AWS Site-to-Site VPN and Accelerated Site-to-Site VPN Connection pricing.
You are charged for data transfer out from Amazon EC2 to the internet. For more information, see Data Transfer on the Amazon EC2 On-Demand Pricing page.
When you create an accelerated VPN connection, we create and manage two accelerators on your behalf. You are charged an hourly rate and data transfer costs for each accelerator. For more information, see AWS Global Accelerator pricing.
How AWS Site-to-Site VPN works
A Site-to-Site VPN connection offers two VPN tunnels between a virtual private gateway or a transit gateway on the AWS side, and a customer gateway (which represents a VPN device) on the remote (on-premises) side.
Virtual private gateway
A virtual private gateway is the VPN concentrator on the Amazon side of the Site-to-Site VPN connection. You create a virtual private gateway and attach it to the VPC from which you want to create the Site-to-Site VPN connection.
Transit gateway
A transit gateway is a transit hub that you can use to interconnect your virtual private clouds (VPC) and on-premises networks. For more information, see Amazon VPC Transit Gateways. You can create a Site-to-Site VPN connection as an attachment on a transit gateway.
Customer gateway device
A customer gateway device is a physical device or software application on your side of the Site-to-Site VPN connection. You configure the device to work with the Site-to-Site VPN connection. For more information, see Your customer gateway device.
Customer gateway
A customer gateway is a resource that you create in AWS that represents the customer gateway device in your on-premises network. When you create a customer gateway, you provide information about your device to AWS. For more information, see Customer gateway options for your Site-to-Site VPN connection.
Single Site-to-Site VPN connection
The VPC has an attached virtual private gateway, and your on-premises (remote) network includes a customer gateway device, which you must configure to enable the Site-to-Site VPN connection. You set up the routing so that any traffic from the VPC bound for your network is routed to the virtual private gateway.
Single Site-to-Site VPN connection with a transit gateway
The VPC has an attached transit gateway, and your on-premises (remote) network includes a customer gateway device, which you must configure to enable the Site-to-Site VPN connection. You set up the routing so that any traffic from the VPC bound for your network is routed to the transit gateway.
Multiple Site-to-Site VPN connections
The VPC has an attached virtual private gateway, and you have multiple Site-to-Site VPN connections to multiple on-premises locations. You set up the routing so that any traffic from the VPC bound for your networks is routed to the virtual private gateway.
You can also use this scenario to create Site-to-Site VPN connections to multiple geographic locations and provide secure communication between sites. For more information, see Providing secure communication between sites using VPN CloudHub.
Multiple Site-to-Site VPN connections with a transit gateway
The VPC has an attached transit gateway, and you have multiple Site-to-Site VPN connections to multiple on-premises locations. You set up the routing so that any traffic from the VPC bound for your networks is routed to the transit gateway.
You can also use this scenario to create Site-to-Site VPN connections to multiple geographic locations and provide secure communication between sites.
Site-to-Site VPN connection with AWS Direct Connect
The VPC has an attached virtual private gateway, and connects to your on-premises (remote) network through AWS Direct Connect. You can configure an AWS Direct Connect public virtual interface to establish a dedicated network connection between your network to public AWS resources through a virtual private gateway. You set up the routing so that any traffic from the VPC bound for your network routes to the virtual private gateway and the AWS Direct Connect connection.
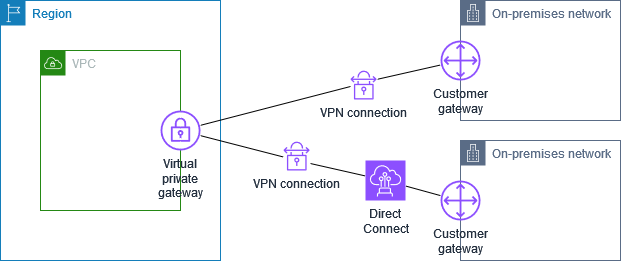
Note :
When both AWS Direct Connect and the VPN connection are set up on the same virtual private gateway, adding or removing objects might cause the virtual private gateway to enter the ‘attaching’ state. This indicates a change is being made to internal routing that will switch between AWS Direct Connect and the VPN connection to minimize interruptions and packet loss. When this is complete, the virtual private gateway returns to the ‘attached’ state.
Private IP Site-to-Site VPN connection with AWS Direct Connect
With a private IP Site-to-Site VPN you can encrypt AWS Direct Connect traffic between your on-premises network and AWS without the use of public IP addresses. Private IP VPN over AWS Direct Connect ensures that traffic between AWS and on-premises networks is both secure and private, allowing customers to comply with regulatory and security mandates.
View Site-to-Site VPN logs configuration
To view current tunnel logging settings
- Open the Amazon VPC console at https://console.aws.amazon.com/vpc/.
- In the navigation pane, choose Site-to-Site VPN Connections.
- Select the VPN connection that you want to view from the VPN connections list.
- Choose the Tunnel details tab.
- Expand the Tunnel 1 options and Tunnel 2 options sections to view all tunnel configuration details.
- You can view the current status of the logging feature under Tunnel VPN log, and the currently configured CloudWatch log group (if any) under CloudWatch log group.
To view current tunnel logging settings on a Site-to-Site VPN connection using the AWS command line or API
Monitoring VPN connections using AWS Health events
AWS Site-to-Site VPN automatically sends notifications to the AWS AWS Health Dashboard (PHD), which is powered by the AWS Health API. This dashboard requires no setup, and is ready to use for authenticated AWS users. You can configure multiple actions in response to event notifications through the AWS Health Dashboard.
The AWS Health Dashboard provides the following types of notifications for your VPN connections:
